
Adidas, Panera Bread, Saks 5th Avenue, Under Armor (My Fitness Pal), FedEx, Aetna, VTech, Exactis — What do these companies have in common aside from a well-known brand? They have all reported data breaches in the first half of 2018. This list is only a fraction of the breaches that have been reported (Just imagine how many you haven’t heard about). Why does this continue to happen? Are the hackers are getting smarter? To some extent, sure, there is a precedence for that line of thinking. They are also grouping up and feeding off each other to take down their next target… two heads are better than one, right? In addition, the hackers are taking advantage of security holes reported in the past that have never been corrected. Finally, what also plays into these continued breaches, are the risk assessments themselves: The IT audit discovery process, recommendations, and execution of items reported, the compliance follow up, and the Ace that wasn’t included.
Discovery Process
The discovery process is the most important part of the assessment. If you don’t know what a customer has, how can you evaluate their network? Now, I am not disrespecting any IT Risk Assessment companies so please don’t go all ego maniacal on me. I have worked with many that have been very thorough, but I have also found a few who don’t dig deep enough or really don’t know which questions to ask to peel back the layers of the onion. Your IT Risk Assessment team should not only include accountants, financial gurus, and insurance specialists, but expert level security and infrastructure members. A STRONG IT presence (This is your Ace — think CCDA, CISSP, MSCE types plus many years working various IT roles across the industry, certifications alone are not enough) will make the difference when entering and completing the discovery phase of an audit.
Listed in the table below are typical items requested and reviewed during an audit for a risk assessment:
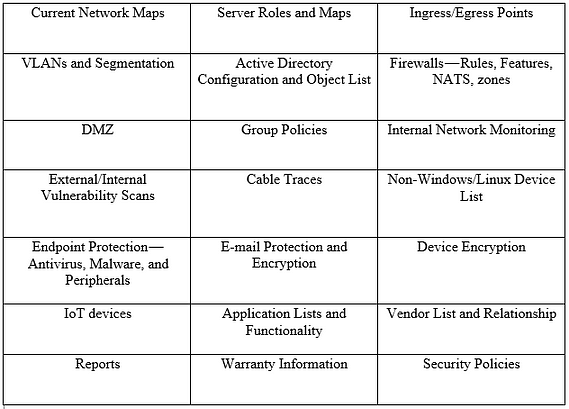
There are many others but that is enough to give you a view. It is easy to request and receive that documentation but how do you know that it is accurate without knowing what has been missed and how to verify it?
If a customer has a mix of Windows Server 2008 R2 and Windows Server 2016, what domain functional level are they on and why? Is auditing and/or verbose logging enabled? If they have Windows 7 and Windows 10 what version(s) of NTLM over SMB are they using to connect to file shares if at all? Are they using TLS or SSL for website, email and database access and what version? Have they patched devices or put best practices in place to protect the network from known reported and utilized vulnerabilities (i.e. WannaCry, KRACK, Heart bleed, Meltdown, Spectre, etc.)?
The point is you can ask for items in a list and then be provided with the answers and documentation, but you can’t assume the information is correct. Part of the discovery must include the verification of what the client network encompasses including all assests and if it has been properly implemented or you can’t accurately estimate risk.
Recommendations and Execution
After the discovery phase has been completed, a findings report will be yielded. The findings report should reveal at high level what systems are in place and how each is configured, compliant, and secure. After the high-level presentation, there should be granular items listed that showcase the details of the network broken out into pieces making it organized and easier to consume. This is another area where the Ace also makes a huge impact. Within each section, recommendations and actions items will be listed to bring the client’s network up to the standards and compliance needed in addition to what is required for their industry (Yes, some industries are more highly regulated than others). Some of these recommendations may be as easy as adding software to harden end points for av/malware protection. Others may be simple port closings or password changes. There are times when a full-scale network redesign is needed to update all switches/routers/firewalls.
Every report I have ever seen has always contained a list of items that need to be executed by the client in various capacities. The risk assessment team will then take the current posture and provide the risk analysis with statistics, models, and financial estimates. The Ace will know where pressure needs to be applied to handily reduce the organizations risk including potential financial and data loss. Proven methodology along with tips and instructions will help the client reach their risk assessment goals. In addition, industry best practices and standard hardening configurations provided by the Ace will not only reduce the risk but also protect the client and their data from being affected by past security breaches reported and possible future attacks.
Follow up for Compliance
Once the audit has been completed and the risk assessment delivered (hopefully with threat models), a follow up date should be scheduled to ensure that items found have been mitigated or additional systems have been implemented to meet the requirements. These meetings should occur quarterly after the risk assessment and should not wait until an annual review or the next assessment. Again, this is where the Ace is indispensable. Instead of just reviewing the check boxes and assuming all is well, a deeper dive is necessary.
- Review new IVA/EVA scans
- Review reports and configuration of All systems (including newly implemented)
- Review changes in group policy
- Review network and firewall rule changes
- Run scripts or powershell commands to verify information
- Run sniffers to inspect traffic
There are multiple items to dive into but you get the idea. We want to verify from a technical stand point that what has been implemented or “fixed” has actually been completed and/or set up properly. Additionally, you have to make sure that your mitigations are not creating further risk which I liken to regression testing that is done in software development. Only a technical expert, our Ace, can review the current posture to verify the client has reduced their risk by following the strategy outlined in the initial risk assessment.
Final Thought
In the age of “everything is connected” and as we move further and further into the cloud, we have to be sure that we are holistically approaching security and reducing exposure risk. Hosting applications and data in any way is a gamble so wouldn’t you rather have an Ace up you sleeve? Be sure to really vet your partners and do your due diligence when audits come back with issues to address. Take care of them as quickly as possible. If you don’t, you may as well flush that money that you spent down the drain.
About the Author

Khaled Antar
VP, Infrastructure





